29Aug
06Jun
Cloud Communications Provider Selection
Communicate, Collaborate, Connect
Moving or expanding communications services to the cloud can seem daunting for any company. But if you know what to look for from a provider, the task of choosing a unified communications as a service (UCaaS) solution can be made with greater confidence. Like...
31May
Windows 7 Upgrade vs Replacement
Microsoft Windows 7 is End of Life on January 14, 2020.
As a result, your organization will need to determine whether upgrading Windows 7 Computers is sufficient or replacement of devices is necessary before this date. End of Life is the phrase used by a vendor to...
03May
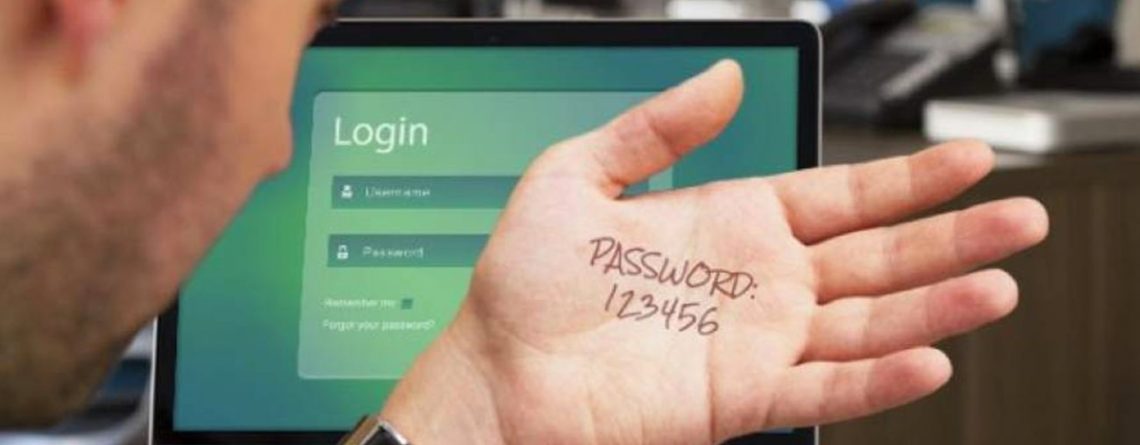
It’s World Password Day. Generate a fresh one.
Protect your Digital Life
Password security is something that many people have problems with. Having a secure password for each of your online accounts is important. Because if a scammer gets just one password, they can begin to access your other accounts. That’s why it’s important...
01Dec
Should Your Company Outsource to a Tech Provider?
A tech provider delivers the IT expertise small businesses need at a much lower cost than hiring IT staff. They can recommend, install, and manage technology according to business’ objectives and core competencies and ensure that critical data is safe.
That’s why nearly 70% of...
10Oct
Ransomware Is Everywhere These Days
Cyber security threats like ransomware can seem sophisticated. But protecting yourself from them is less like rocket science. Really, it's more like safe driving on the highway. But it doesn’t require expertise in the field of computer security or digital forensics. And the tools...
25Jan
What’s New in Windows 10 Pro?
Windows 10 Pro gives you and your business the freedom to do great things. But Windows 10 Professional isn’t just for cubicle dwellers who have no choice in the matter. While users who own a “professional” PC like the
05May
10 Year Celebration
"There's no luck in business. There's only drive, determination, and more drive." - Sophie Kinsella
24Apr
Bridgewater Technet joins forces with Profulgent Technology
In today’s fast paced world of technology, Profulgent Technology recognizes the need for the highest level of service. As a result, they are continuously looking for opportunities to expand and strengthen their team.
Hazlet, NJ, May 1, 2015: Profulgent Technology and Bridgewater Technet have...
23Feb